本主題說明如何將加密金鑰匯入 Cloud HSM 或 Cloud Key Management Service,做為新的金鑰版本。
如要進一步瞭解如何匯入金鑰,包括限制和規定,請參閱金鑰匯入。
完成本主題中的步驟需要 5 到 10 分鐘,不包括「事前準備」步驟。手動包裝金鑰會增加工作複雜度。
事前準備
建議您建立新專案來測試這項功能,方便在測試後清除資料,並確保您具備足夠的「身分與存取權管理」(IAM) 權限來匯入金鑰。
匯入金鑰前,請先準備好專案、本機系統和金鑰。
準備專案
-
In the Cloud de Confiance console, on the project selector page, select or create a Cloud de Confiance project.
Roles required to select or create a project
- Select a project: Selecting a project doesn't require a specific IAM role—you can select any project that you've been granted a role on.
-
Create a project: To create a project, you need the Project Creator
(
roles/resourcemanager.projectCreator), which contains theresourcemanager.projects.createpermission. Learn how to grant roles.
-
Verify that billing is enabled for your Cloud de Confiance project.
-
Enable the required API.
Roles required to enable APIs
To enable APIs, you need the Service Usage Admin IAM role (
roles/serviceusage.serviceUsageAdmin), which contains theserviceusage.services.enablepermission. Learn how to grant roles. -
Install the Google Cloud CLI.
-
設定 gcloud CLI 以使用您的聯合身分。
詳情請參閱「 使用聯合身分登入 gcloud CLI」。
-
如要初始化 gcloud CLI,請執行下列指令:
gcloud init -
執行匯入作業的使用者需要下列 IAM 權限,才能建立金鑰環、金鑰和匯入工作。如果使用者不是專案擁有者,您可以將下列兩項預先定義的角色指派給使用者:
roles/editorroles/cloudkms.importer
如要進一步瞭解 Cloud KMS 適用的 IAM 角色和權限,請參閱「權限和角色」。
- 如要允許 Google Cloud CLI 在將金鑰傳輸至 Cloud de Confiance by S3NS前自動包裝金鑰,您必須在本機系統安裝 Pyca 密碼編譯程式庫。匯入工作會使用 Pyca 程式庫,在將金鑰傳送至 Cloud de Confiance之前,先在本機包裝並保護金鑰。
- 如要手動包裝金鑰,請務必設定 OpenSSL 以手動包裝金鑰。
「防護等級」會指出金鑰是否保留在軟體、HSM 或外部金鑰管理系統中。金鑰內容無法從其中一個儲存環境移至另一個環境。所有金鑰版本都具有相同的保護等級。
「用途」會指出金鑰版本是用於對稱式加密、非對稱式加密,還是非對稱式簽署。金鑰用途會限制可用於建立金鑰版本的演算法。金鑰的所有版本用途都相同。
前往 Cloud de Confiance 控制台的「Key Management」頁面。
按一下 [Create key ring] (建立金鑰環)。
在「Key ring name」(金鑰環名稱) 欄位中輸入金鑰環的名稱。
在「位置類型」下方,選取位置類型和位置。
按一下「Create」(建立)。「建立金鑰」頁面隨即開啟。
在「Key name」(金鑰名稱) 欄位中,輸入金鑰的名稱。
在「Protection level」(防護等級) 中,選取「Software」(軟體) 或「HSM」,然後按一下「Continue」(繼續)。
在「Key material」(金鑰內容) 部分,選取「Imported key」(匯入的金鑰),然後按一下「Continue」(繼續)。 這樣一來,系統就不會建立初始金鑰版本。
設定金鑰的「用途」和「演算法」,然後按一下「繼續」。
選用:如要讓這個金鑰只包含匯入的金鑰版本,請選取「將金鑰版本設定為僅限匯入」。這樣可避免您在 Cloud KMS 中誤建新的金鑰版本。
選用:如果是匯入的金鑰,系統預設會停用自動輪替功能。 如要啟用自動輪替,請從「金鑰輪替週期」欄位選取值。
啟用自動輪替功能後,系統會在 Cloud KMS 中產生新的金鑰版本,輪替後匯入的金鑰版本將不再是預設金鑰版本。
點選「建立」。
建立目標金鑰環。如要匯入 Cloud HSM 金鑰,請選取支援 Cloud HSM 的位置。
gcloud kms keyrings create KEY_RING \ --location LOCATION
進一步瞭解如何建立金鑰環。
建立目標鍵。
- 指定金鑰的用途。
- 使用
--skip-initial-version-creation標記,避免建立初始版本。 - 選用:使用
--import-only旗標,防止在 Cloud KMS 中建立新版本。 - 選用:請勿指定輪替政策。如果啟用自動輪替功能,系統會在 Cloud KMS 中產生新的金鑰版本,輪替後匯入的金鑰版本就不再是預設金鑰版本。如果指定
--import-only旗標,則無法指定輪替政策。
gcloud kms keys create KEY_NAME \ --location LOCATION \ --keyring KEY_RING \ --purpose PURPOSE \ --skip-initial-version-creation \ --import-only
您可以進一步瞭解如何建立 Cloud KMS 金鑰或 Cloud HSM 金鑰。
建立新的金鑰環:
curl "https://cloudkms.googleapis.com/v1/projects/PROJECT_ID/locations/LOCATION/keyRings?keyRingId=KEY_RING" \ --request "POST" \ --header "authorization: Bearer TOKEN" \ --header "content-type: application/json" \ --header "x-goog-user-project: PROJECT_ID" \ --data "{}"詳情請參閱
KeyRing.createAPI 說明文件。建立僅供匯入的空白金鑰:
curl "https://cloudkms.googleapis.com/v1/projects/PROJECT_ID/locations/LOCATION/keyRings/KEY_RING/cryptoKeys?cryptoKeyId=KEY_NAME&skipInitialVersionCreation=true&importOnly=true" \ --request "POST" \ --header "authorization: Bearer TOKEN" \ --header "content-type: application/json" \ --header "x-goog-user-project: PROJECT_ID" \ --data "{"purpose":"PURPOSE", "versionTemplate":{"protectionLevel":"PROTECTION_LEVEL","algorithm":"ALGORITHM"}}"詳情請參閱
CryptoKey.createAPI 說明文件。前往 Cloud de Confiance 控制台的「Key Management」頁面。
按一下目標金鑰環的名稱。
將「防護等級」設為「軟體」或「HSM」。請使用與目標金鑰相同的防護等級。
按一下 [Create import job] (建立匯入工作)。
在「Name」(名稱) 欄位中,輸入匯入工作的名稱。
在「Import method」下拉式選單中,將匯入方法設為「3072 bit RSA」或「4096 bit RSA」。
點選「建立」。
- 使用與目標金鑰相同的金鑰環和位置。
- 將防護等級設為
software或hsm。 - 將匯入方法設為
rsa-oaep-3072-sha1-aes-256、rsa-oaep-4096-sha1-aes-256、rsa-oaep-3072-sha256-aes-256、rsa-oaep-4096-sha256-aes-256、rsa-oaep-3072-sha256或rsa-oaep-4096-sha256。 前往 Cloud de Confiance 控制台的「Key Management」頁面。
按一下包含匯入工作的金鑰環名稱。
按一下頁面頂端的 [Import Jobs] (匯入工作) 分頁標籤。
狀態會顯示在該匯入作業名稱旁的 [Status] (狀態) 下方。
- 請只授予主要管理員
importjobs.create權限。 - 將特定匯入工作的
importjobs.useToImport權限授予將使用該工作匯入金鑰的作業人員。 - 建立匯入工作時,請指定透過該工作匯入的金鑰版本的防護等級和演算法。
用途為
ENCRYPT_DECRYPT的金鑰會使用google-symmetric-encryption演算法,長度為 32。用途為
ASYMMETRIC_DECRYPT或ASYMMETRIC_SIGN的金鑰支援多種演算法和長度。金鑰建立後就無法變更用途,但後續的金鑰版本長度可以與初始金鑰版本不同。
在Cloud de Confiance 控制台中開啟「Key Management」(金鑰管理) 頁面。
按一下包含匯入工作的金鑰環名稱。系統會顯示目標金鑰,以及金鑰環上的任何其他金鑰。
按一下目標金鑰的名稱,然後點選「匯入金鑰版本」。
在「Select import job」(選取匯入工作) 下拉式選單中,選取您的匯入工作。
在「Upload the wrapped key」(上傳經過包裝的金鑰) 選取工具中,選取您已包裝的金鑰。
如果您要匯入非對稱金鑰,請在「Algorithm」(演算法) 下拉式選單中選取某個演算法。「Import key version」(匯入金鑰版本) 頁面外觀會像這樣:
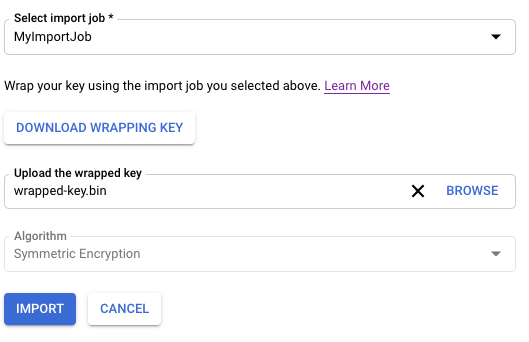
按一下「匯入」。
IMPORT_JOB_ID:對應匯入作業的完整資源名稱。
ALGORITHM:要匯入的金鑰
algorithm,類型為CryptoKeyVersionAlgorithm。WRAPPED_KEY:以 Base64 格式手動包裝的金鑰。
在Cloud de Confiance 控制台中開啟「Key Management」(金鑰管理) 頁面。
按一下包含匯入工作的金鑰環名稱。
按一下頁面頂端的 [Import Jobs] (匯入工作) 分頁標籤。
狀態會顯示在該匯入作業名稱旁的 [Status] (狀態) 下方。
- 只能重新匯入先前匯入的
CryptoKeyVersions。 - 如果先前已成功匯入金鑰內容,重新匯入的金鑰內容必須與原始金鑰內容完全相符。
CryptoKeyVersions,在發布這項功能前刪除的CryptoKeyVersions無法重新匯入。如果版本符合重新匯入資格,CryptoKeyVersion的reimport_eligible欄位會顯示true,否則會顯示false。前往 Cloud de Confiance 控制台的「Key Management」頁面。
按一下金鑰環名稱,該金鑰環包含您要重新匯入金鑰版本的金鑰。
按一下您要重新匯入金鑰版本的金鑰。
按一下要重新匯入的金鑰版本旁邊的三點圖示。
選取「重新匯入金鑰版本」
在「Select import job」(選取匯入工作) 下拉式選單中,選取您的匯入工作。
在「Upload the wrapped key」(上傳經過包裝的金鑰) 選取工具中,選取您已包裝的金鑰。這個金鑰必須與原始金鑰內容相符。
按一下「重新匯入」。
使用原始金鑰材料重新匯入金鑰版本。
gcloud kms keys versions import \ --location LOCATION \ --keyring KEY_RING \ --key KEY_NAME \ --version KEY_VERSION \ --algorithm ALGORITHM \ --import-job IMPORT_JOB \ --target-key-file PATH_TO_KEY \
在
cryptoKeyVersions.import方法的要求主體中,將cryptoKeyVersion欄位設為要匯入的版本金鑰版本名稱。這必須是加密金鑰的子項。在要求主體中,將
algorithm欄位設為待匯入金鑰的演算法。這個值必須與原始金鑰版本的演算法相符。algorithm欄位的類型為CryptoKeyVersionAlgorithm。在要求主體中,將
wrappedKeyMaterial欄位設為您已包裝的金鑰內容。呼叫
cryptoKeyVersions.import方法。cryptoKeyVersions.import回應的類型為CryptoKeyVersion。金鑰成功匯入後的狀態為ENABLED,接著您即可在 Cloud KMS 中使用該金鑰。- 驗證匯入的金鑰。確認匯入的金鑰內容與原始金鑰相同後,您就可以使用該金鑰簽署或保護資料。
- 排解金鑰匯入失敗問題。
準備本機系統
選擇下列其中一個選項,準備好本機系統。建議大多數使用者採用自動金鑰包裝。
準備金鑰
確認金鑰的演算法和長度受到支援。金鑰可用的演算法取決於金鑰是否用於對稱式加密、非對稱式加密或非對稱式簽署,以及金鑰是儲存在軟體還是 HSM 中。您會在匯入要求中指定金鑰的演算法。
此外,您也必須驗證金鑰的編碼方式,並視需要進行調整。
金鑰版本建立或匯入後,就無法變更下列項目:
如果您沒有要匯入的金鑰,但想驗證匯入金鑰的程序,可以使用下列指令在本地系統上建立對稱金鑰:
openssl rand 32 > ${HOME}/test.bin
請僅將這組金鑰用於測試。以這種方式建立的金鑰可能不適合用於實際工作環境。
如需手動包裝金鑰,請先完成這項作業,再繼續本主題中的程序。
建立目標金鑰和金鑰環
Cloud KMS 金鑰是容器物件,內含零或多個金鑰版本。每個金鑰版本都包含加密金鑰。
將金鑰匯入 Cloud KMS 或 Cloud HSM 時,匯入的金鑰會成為現有 Cloud KMS 或 Cloud HSM 金鑰的新金鑰版本。在本主題的其餘部分,這個金鑰稱為「目標金鑰」。您必須先建立目標金鑰,才能將金鑰內容匯入其中。
匯入金鑰版本不會影響該金鑰的現有版本。不過,建議您在測試金鑰匯入時建立空白金鑰。空白金鑰沒有版本、未啟用,且無法使用。
您可以選擇指定新建立的金鑰只能包含匯入的版本,避免在 Cloud KMS 中意外產生新版本。
金鑰環上存在金鑰;在本主題中,這個金鑰環稱為「目標金鑰環」。目標金鑰環的位置會決定匯入後金鑰內容的可用位置。在某些位置,您無法建立或匯入 Cloud HSM 金鑰。金鑰建立後,就無法移至其他金鑰環或位置。
請按照下列步驟,使用 Google Cloud CLI 或 Cloud de Confiance 控制台,在新的金鑰環上建立空白金鑰。
控制台
gcloud
如要在指令列上使用 Cloud KMS,請先安裝或升級至最新版 Google Cloud CLI。
Go
如要執行這段程式碼,請先設定 Go 開發環境,並安裝 Cloud KMS Go SDK。
Java
如要執行這段程式碼,請先設定 Java 開發環境,然後安裝 Cloud KMS Java SDK。
Node.js
如要執行這段程式碼,請先設定 Node.js 開發環境,然後安裝 Cloud KMS Node.js SDK。
Python
如要執行這段程式碼,請先設定 Python 開發環境,然後安裝 Cloud KMS Python SDK。
API
這些範例使用 curl 做為 HTTP 用戶端,示範如何使用 API。如要進一步瞭解存取權控管,請參閱「存取 Cloud KMS API」一文。
金鑰環和金鑰現在已存在,但金鑰不含金鑰內容、沒有版本,且未啟用。接著,請建立匯入工作。
建立匯入工作
匯入工作會定義匯入金鑰的特性,包括金鑰匯入後無法變更的屬性。
防護等級會定義透過這項匯入工作匯入的金鑰,是會存放在軟體、HSM 還是外部金鑰管理系統。金鑰匯入後,就無法變更防護等級。
匯入方法會定義用於建立包裝金鑰的演算法,在從本機系統傳輸至目標 Cloud de Confiance 專案的過程中,包裝金鑰會保護匯入的金鑰。您可以選擇 3072 位元或 4096 位元的 RSA 金鑰。除非有特定需求,否則建議使用 3072 位元包裝金鑰。
您可以使用 gcloud CLI、Cloud de Confiance 控制台或 Cloud Key Management Service API 建立匯入工作。
控制台
gcloud
如要在指令列上使用 Cloud KMS,請先安裝或升級至最新版 Google Cloud CLI。
使用下列指令建立匯入工作。
gcloud kms import-jobs create IMPORT_JOB \ --location LOCATION \ --keyring KEY_RING \ --import-method IMPORT_METHOD \ --protection-level PROTECTION_LEVEL
Go
如要執行這段程式碼,請先設定 Go 開發環境,並安裝 Cloud KMS Go SDK。
Java
如要執行這段程式碼,請先設定 Java 開發環境,然後安裝 Cloud KMS Java SDK。
Node.js
如要執行這段程式碼,請先設定 Node.js 開發環境,然後安裝 Cloud KMS Node.js SDK。
Python
如要執行這段程式碼,請先設定 Python 開發環境,然後安裝 Cloud KMS Python SDK。
API
這些範例使用 curl 做為 HTTP 用戶端,示範如何使用 API。如要進一步瞭解存取權控管,請參閱「存取 Cloud KMS API」一文。
如要建立匯入工作,請使用 ImportJobs.create 方法:
curl "https://cloudkms.googleapis.com/v1/projects/PROJECT_ID/locations/LOCATION/keyRings/KEY_RING/importJobs?import_job_id=IMPORT_JOB_ID" \
--request "POST" \
--header "authorization: Bearer TOKEN" \
--header "content-type: application/json" \
--data '{"import_method": "IMPORT_METHOD", "protection_level": "PROTECTION_LEVEL"}'
更改下列內容:
查看匯入工作的狀態
匯入工作的初始狀態為 PENDING_GENERATION。當狀態為 ACTIVE 時,您就可以使用該金鑰匯入金鑰。
匯入工作會在三天後失效。如果匯入工作已過期,您必須建立新的工作。
您可以使用 Google Cloud CLI、Cloud de Confiance 控制台或 Cloud Key Management Service API,查看匯入工作的狀態。
控制台
gcloud
如要在指令列上使用 Cloud KMS,請先安裝或升級至最新版 Google Cloud CLI。
匯入工作處於有效狀態時,您可以使用該工作匯入金鑰。這項作業可能需要幾分鐘才能完成。使用這項指令確認匯入工作是否處於啟用狀態。使用您建立匯入工作時的所在位置和金鑰環。
gcloud kms import-jobs describe IMPORT_JOB \ --location LOCATION \ --keyring KEY_RING \ --format="value(state)"
輸出結果會與下列內容相似:
state: ACTIVE
Go
如要執行這段程式碼,請先設定 Go 開發環境,並安裝 Cloud KMS Go SDK。
Java
如要執行這段程式碼,請先設定 Java 開發環境,然後安裝 Cloud KMS Java SDK。
Node.js
如要執行這段程式碼,請先設定 Node.js 開發環境,然後安裝 Cloud KMS Node.js SDK。
Python
如要執行這段程式碼,請先設定 Python 開發環境,然後安裝 Cloud KMS Python SDK。
API
這些範例使用 curl 做為 HTTP 用戶端,示範如何使用 API。如要進一步瞭解存取權控管,請參閱「存取 Cloud KMS API」一文。
如要檢查匯入工作的狀態,請使用
ImportJobs.get
方法:
curl "https://cloudkms.googleapis.com/v1/projects/PROJECT_ID/locations/LOCATION/keyRings/KEY_RING/importJobs/IMPORT_JOB_ID" \
--request "GET" \
--header "authorization: Bearer TOKEN"
匯入工作啟用後,您就能發出匯入金鑰的要求。
防止修改匯入工作
匯入工作會決定匯入金鑰的許多特徵,包括金鑰的演算法,以及匯入的金鑰是 HSM 金鑰還是軟體金鑰。您可以設定 IAM 權限,禁止使用者建立匯入工作,但允許他們使用匯入工作匯入金鑰。
在匯入工作到期前,如果使用者擁有 importjobs.useToImport,但沒有特定匯入工作的 importjobs.create 權限,則可以匯入金鑰,但無法修改匯入工作的特性。
匯入金鑰
查看匯入工作的狀態後,即可提出匯入要求。
您可以使用不同的標記提出匯入要求,具體取決於您是否希望 Google Cloud CLI 自動包裝金鑰,或是您是否已手動包裝金鑰。
無論您是手動或自動包裝金鑰,都必須將演算法設為支援的演算法,且該演算法須符合待匯入金鑰的長度,並指定金鑰用途。
自動包裝及匯入金鑰
如要使用自動包裝功能,必須使用 Google Cloud CLI。請使用類似下列的指令。將 --target-key-file 設為要包裝及匯入的未包裝金鑰位置。請勿設定 --wrapped-key-file。
您可以選擇將 --public-key-file 標記設為已下載公開金鑰的位置。匯入大量金鑰時,這項設定可避免在每次匯入時下載公開金鑰。舉例來說,您可以編寫指令碼,下載公開金鑰一次,然後在匯入每個金鑰時提供公開金鑰位置。
gcloud kms keys versions import \
--import-job IMPORT_JOB \
--location LOCATION \
--keyring KEY_RING \
--key KEY_NAME \
--algorithm ALGORITHM \
--target-key-file PATH_TO_UNWRAPPED_KEY
金鑰會由與匯入工作相關聯的包裝金鑰包裝,然後傳輸至 Cloud de Confiance,並匯入為目標金鑰的新金鑰版本。
匯入手動包裝的金鑰
請按照本節的操作說明,匯入手動包裝的金鑰。將 --wrapped-key-file 設為您手動包裝的金鑰位置。請勿設定 --target-key-file。
您可以選擇將 --public-key-file 標記設為已下載公開金鑰的位置。匯入大量金鑰時,這項設定可避免在每次匯入時下載公開金鑰。舉例來說,您可以編寫指令碼,下載公開金鑰一次,然後在匯入每個金鑰時提供公開金鑰位置。
控制台
gcloud
如要在指令列上使用 Cloud KMS,請先安裝或升級至最新版 Google Cloud CLI。
請使用類似下列的指令。
gcloud kms keys versions import \ --import-job IMPORT_JOB \ --location LOCATION \ --keyring KEY_RING \ --key KEY_NAME \ --algorithm ALGORITHM \ --wrapped-key-file PATH_TO_WRAPPED_KEY
詳情請參閱 gcloud kms keys versions import --help 指令的輸出內容。
Go
如要執行這段程式碼,請先設定 Go 開發環境,並安裝 Cloud KMS Go SDK。
Java
如要執行這段程式碼,請先設定 Java 開發環境,然後安裝 Cloud KMS Java SDK。
Node.js
如要執行這段程式碼,請先設定 Node.js 開發環境,然後安裝 Cloud KMS Node.js SDK。
Python
如要執行這段程式碼,請先設定 Python 開發環境,然後安裝 Cloud KMS Python SDK。
API
這些範例使用 curl 做為 HTTP 用戶端,示範如何使用 API。如要進一步瞭解存取權控管,請參閱「存取 Cloud KMS API」一文。
使用 cryptoKeyVersions.import 方法匯入金鑰。
curl "https://cloudkms.googleapis.com/v1/projects/PROJECT_ID/locations/LOCATION/keyRings/KEY_RING/cryptoKeys/KEY_NAME/cryptoKeyVersions:import" \
--request "POST" \
--header "authorization: Bearer TOKEN" \
--header "content-type: application/json" \
--data '{"importJob": "IMPORT_JOB_ID", "algorithm": "ALGORITHM", "wrappedKey": "WRAPPED_KEY"}'
更改下列內容:
系統會發出金鑰匯入要求。你可以監控狀態。
查看已匯入金鑰版本的狀態
已匯入金鑰版本的初始狀態為 PENDING_IMPORT。當狀態為 ENABLED 時,代表金鑰版本已成功匯入。如果匯入失敗,狀態會顯示 IMPORT_FAILED。
您可以使用 Google Cloud CLI、Cloud de Confiance 控制台或 Cloud Key Management Service API,查看匯入要求的狀態。
控制台
gcloud
如要在指令列上使用 Cloud KMS,請先安裝或升級至最新版 Google Cloud CLI。
請使用 versions list 指令來查看狀態。使用您在本主題中稍早建立的相同位置、目標金鑰環和目標金鑰。
gcloud kms keys versions list \ --keyring KEY_RING \ --location LOCATION \ --key KEY_NAME
Go
如要執行這段程式碼,請先設定 Go 開發環境,並安裝 Cloud KMS Go SDK。
Java
如要執行這段程式碼,請先設定 Java 開發環境,然後安裝 Cloud KMS Java SDK。
Node.js
如要執行這段程式碼,請先設定 Node.js 開發環境,然後安裝 Cloud KMS Node.js SDK。
Python
如要執行這段程式碼,請先設定 Python 開發環境,然後安裝 Cloud KMS Python SDK。
API
這些範例使用 curl 做為 HTTP 用戶端,示範如何使用 API。如要進一步瞭解存取權控管,請參閱「存取 Cloud KMS API」一文。
呼叫 ImportJob.get 方法,然後查看 state 欄位。如果 state 為 PENDING_GENERATION,代表匯入工作仍在建立中。請定期重新查看狀態,直到狀態變成 ACTIVE 為止。
匯入初始金鑰版本後,金鑰的狀態會變更為「有效」。如果是對稱金鑰,您必須將匯入的金鑰版本設為主要版本,才能使用金鑰。
對稱金鑰:設定主要版本
匯入對稱金鑰時必須執行這個步驟,非對稱金鑰則不適用。非對稱金鑰沒有主要版本。您必須使用 Google Cloud CLI 設定主要版本。
gcloud kms keys set-primary-version KEY_NAME\
--location=LOCATION\
--keyring=KEY_RING\
--version=KEY_VERSION
重新匯入先前刪除的金鑰
Cloud Key Management Service 支援金鑰重新匯入作業,可讓您提供原始金鑰內容,將先前匯入且處於 DESTROYED 或 IMPORT_FAILED 狀態的金鑰版本還原為 ENABLED 狀態。如果因為初始匯入失敗而從未匯入原始金鑰內容,則可提供任何金鑰內容。
限制
軟體和 Cloud HSM 金鑰可以重新匯入,但外部金鑰無法重新匯入。
重新匯入已刪除的金鑰
按照「建立匯入工作」中的步驟,建立用於重新匯入的 ImportJob。您可以使用現有 ImportJob 或新 ImportJob,只要防護等級與原始防護等級相符即可。
控制台
gcloud
如要在指令列上使用 Cloud KMS,請先安裝或升級至最新版 Google Cloud CLI。
API
這些範例使用 curl 做為 HTTP 用戶端,示範如何使用 API。如要進一步瞭解存取權控管,請參閱「存取 Cloud KMS API」一文。

